We paid Ransom32, the virus malware that encrypts all your files and demands payment within a number of days to recover them, and we got our files back. Ish. From frantic googling, to panicked backup recovery attempts, to resignation and payment, here’s how it went down…
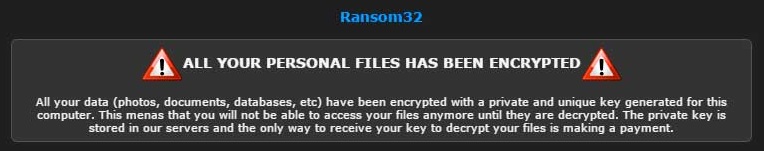
On a recent Wednesday morning, one person in our small office apparently clicked on a bad advertisement seen online. Somehow, through an exploit in NW.js, the virus was able to run, install itself, and start encrypting files in the background. It wasn’t until later in the afternoon, after it had already encrypted all the files it could access, that it then popped up it’s screen demanding payment:
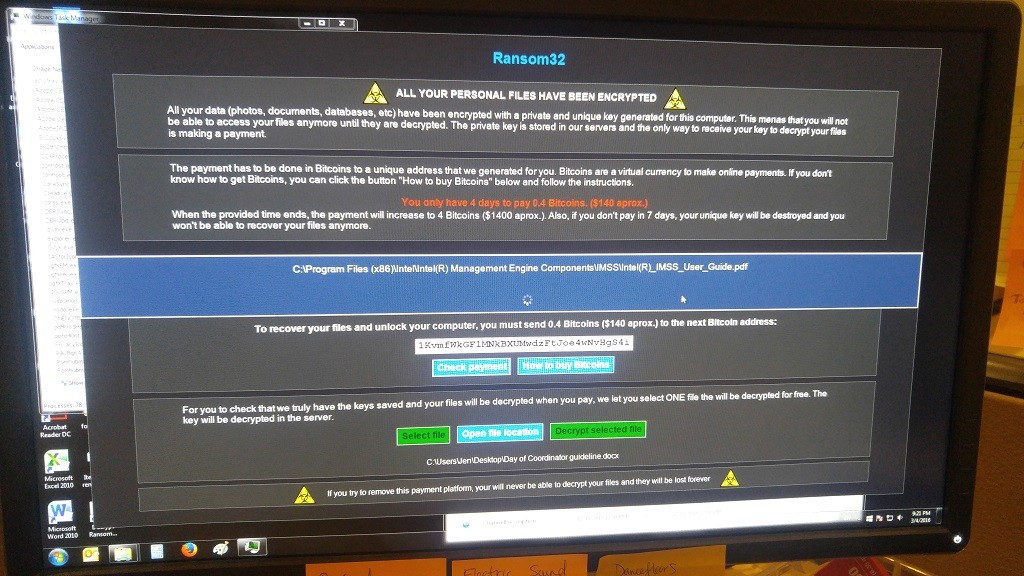
As you can see from the example screenshot above, there’s 4 days to pay the first level of ransom to get your files decrypted. Then the price goes up 10 times. When we had our virus it was 0.4 Bitcoin (“btc”) or about $162 USD. If you don’t pay within ten days the virus claims you won’t be able to recover at all.
The bad, very bad, news was that it even accessed network drives and it encrypted every one of those it could find. Our office uses a common network shared folder and a personal network folder hosted on a Windows Server 2008 file server. The common folder is available to anyone and everyone is instructed to place files there that aren’t specifically personal. All other files go to the personal folder. Employees don’t really use their own computers for storing files at all unless they’re temporary–they don’t even really use their Documents folders–it’s all on their personal shared folder. The idea is that the office has a central backup on the file server so backups don’t need to be setup on the workstations which was probably a mistake in hindsight.
Tip: Enable “Previous Versions” and setup a Windows Backup and Restore schedule on all workstations possible. This will act as a first line of defense in your backup strategy. In the case of Ransom32, it avoided encrypting Windows files, including backups, which means you could recover from the workstation backups once you have removed the virus.
Initially, we figured there would be some tool to recover our files. After a lot of research, we couldn’t find a one. That’s because it uses real, legitimate, full-strength AES encryption. The FBI/CIA/NSA might have the resources to break this encryption but mere mortals such as you and I do not. More details on the encryption process here.
The even worse news was the state of our file server backups. Our initial thought was no problem, just restore from backups. We might lose a day of work, but given the severity we could already see with this virus, we could deal with that. The virus had gone to work on a Wednesday, most of the company was at a tradeshow on a Thursday, and we realized we had to move on the virus on the Friday. By that time, as fate would have it, the file server backups had rotated out or somehow lost previous backups so that we only had backups from the current day and the previous day. Ugh. We tried various things like checking for “Previous Versions” in Windows Explorer or Googling for how to find older backups but we couldn’t.
Tip: Check if you need to pause backups as soon as you hear about having a virus like Ransom32. If you’re unlucky, you may get the virus the day on the day your backup schedule drops off the last good day of backups. Pause your backups as soon as possible, ideally make a copy immediately just to be safe, and remember to un-pause when everything is done.
After realizing our backups had failed us, we contacted the police and RCMP (Canada’s version of the FBI). Strangely, while empathetic and trying to help, they weren’t really interested and apparently had no means or resources to help us. We were directed to contact our ISP first, which was an epic waste of time, as we were told they probably had a security process we should first go through for this situation. They did not, or at least the person we talked to didn’t understand. Our ISP redirected us to our anti-virus company. They couldn’t do anything because our files were legitimately encrypted. We called a few phone numbers the police and RCMP gave us and no departments seemed to help. One person told me the FBI recommends people just pay up.
Ransom32 provides a way to decrypt one file of your choosing to prove it works before you pay. I did this and it appeared to work so that gave me some confidence the real thing would work if I paid.
The virus demands payment in Bitcoin. I had heard a lot about Bitcoin, knew it was a legitimate currency, but never dealt in it, myself, and neither had anyone else I knew who could help quickly. My boss and I were working late on it but we had pretty much given up. I asked my boss if she wanted to give up, and write off the files and data, and she said that she pretty much had and she left for home shortly after. I had pretty much given up, too, but knowing the accumulated value of years of files and data on those network drives, and that there was still an option to try paying, I still wanted to try the Bitcoin payment to see if the virus would actually do it. I convinced the boss that we might be down about $160 USD if we paid but we would be in no worse position if we tried to pay and it didn’t work. The huge potential upside would be we’d get our files back. Kind of a no-brainer when all the files and data your business relies on for day to day operation might be lost forever.
I started looking at the legitimate Bitcoin providers again. I immediately saw US-based Coinbase and UK-based CEX.IO. At least they were first-world countries, I thought. I initially wanted to go US as I had more confidence in them then the UK (no offence, UK, just a personal bias being on the other side of the pond) so I tried Coinbase. They required all kinds of personal info, which I was willing to fill in, and uploading identification documents. I got scared off with them when they seemed to require some hardcore identification documents like passports or visas. They also had limits on how much I could buy and how soon I could send it so I knew even if I could upload all that I might not have enough time to pay the Ransom32 payment. I then tried CEX.IO which also required personal info and identification document uploads but didn’t require serious documents. They wanted a personal photo, a personal photo holding up the credit card you would be using, and a photo of your drivers license. I did all that and, surprise, they verified it within minutes, really. I was able to buy Bitcoin and send to Ransom32 within about an hour or so.
Tip: Know your legitimate Bitcoin sources. Coinbase is a US-based Bitcoin services provider and CEX.io is a UK-based provider. The other Bitcoin providers you can find online seem pretty sketchy and I never had the confidence to use them. On the downside, Coinbase and CEX.IO require uploading identification documents such as a photo of yourself, a drivers license, etc. They also have limits to how much you can purchase and how soon. I recommend CEX.IO as I was able to sign up, upload identification, get verified, purchase Bitcoin, and send Bitcoin to pay the virus, all in about an hour on a Friday evening around 9pm EST.
So, I paid the virus off, and went back to the infected workstation. I clicked the “Check Payment” button and, as I recall, I had to try a few times and wait in between, maybe 15min total. Finally, it went through and immediately started decrypting all the files. That was a good moment to see that after a full and intense day of trying to work through all of this.
I immediately went to the first few files and checked them out. It looked like it was actually working. By the end of it, we got our files back. Ish. You see, I’m not sure if it was that the virus wasn’t designed to handle network drives safely, but the files we got back from the decryption process were often corrupt. Some were good, but many were bad. Images mostly came back but not pristine. There were visual artifacts in many of them. Word documents sometimes came back but upon opening them we always had to go through the recovery prompt that Word popped up. Even then, some corruption was in the documents. Excel files had the same issues. All PDF files seemed to be corrupt.
Tip: The Ransom32 decryption process is not perfect. There may be corruption in some or even many files. Your best bet is a backup your workstations can’t possibly touch.
When all was said and done we had paid off the Ransom32 virus and got some of our files back. If you were wondering, yes, it did seem to work for us. Just remember, it corrupts many files in the decryption process so your best bet it always having backups that your workstations can’t touch!
I hope you never personally experience having any of the recent rash of ransomware malware but if you do I hope this post has helped. Good luck!
If you have any questions I’m always available via the comments!
Further Reading
- Ransom32:
- Ransomware (Wikipedia)
- Backup (Wikipedia)
- Backup rotation scheme (Wikipedia)
- Rsync.net – Quality off-site backup supporting all platforms and many software for transferring backups
wow, crazy man! interesting stuff. Good reason not to have a NAS attached all the time… Does this affect Mac?i should google that. I have a tertiary backup of 90% of our stuff which sits on the shelf on a 3.5 inch 1TB drive which is immune from just about anything save a house fire or nuclear weapon.
Yeah,so frustrating. We would’ve been saved if we had just one more day of backups. I think right now it only affects Windows but there’s nothing stopping it from affecting every other platform because it’s all web code (html/css/js) that has access to the system through NW.js. If the computer can access your backups so can the virus. So that means only a disconnected backup source is safe. If you have another device that can access your computer, but not the other way around, then that’s a good backup plan, too. It’s like “pull” model (backup source “pulls” your computer’s data) rather than a “push” model (your computer “pushes” your data to the backup source). A completely offline hard drive on the shelf is also a safe alternative, just remember to keep it up to date somehow.